Common RAID levels.
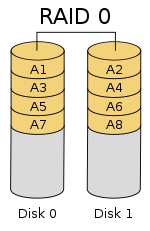
RAID 0
Simply provides enhanced performance. RAID 0 stripes data across multiple disk drives. This system increases throughput by increasing the livelihood that the disk subsystem will be able to fetch different portions of the same file from multiple spindles at the same time.This system has no fault tolerance. Any one of which can fail and ruin the volume .
* High performance ( when data loss is not critical )
RAID 1
Consists of either disk mirroring ( maintaining the same data on multiple disks ) and/or disk duplexing (maintaining mirrors on separate disk controller to eliminate the risk of controller failure.Provides both fault tolerance and greater performance , because the same data can be read from multiple disks or controllers.
* Costly
* Good read and write performance
* Mirroring
* High reliability
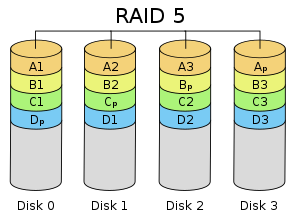
RAID 5
stripes at the block level , it also stripes the parity data across all disks. This eliminate the performance bottleneck of maintaining parity data on one disk, thus enabling the system to perform write operation more quickly. However this can make RAID set rebuilding slower.*Distributed parity
*Spreads data and parity among all N+ drives.
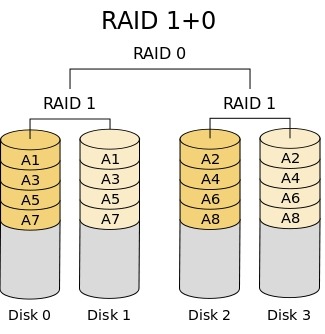
RAID 1+0
* High fault tolerance* High data availability
* Good Read/Write performance
* Very expensive



/about/2000px-RAID_1.svg-57ccc32f5f9b5829f4624b6a.png)